Phishing Scams
The below chart displays the number of phishing attacks incurred from the year 2005 to 2014.
Data Source: Wikipedia
In the field of computer security, phishing is the criminally fraudulent process of attempting to acquire the sensitive information like usernames, passwords and credit card details by masquerading as a trustworthy entity in a communication.
The messages that direct you to a website or phone number may appear to be from a legitimate organization, but in reality, they are designed to be deceptive and
fraudulent. These emails are crafted with the intention of tricking individuals into disclosing personal information. The operators behind these scams aim to steal
your identity, run up unauthorized bills, or even commit crimes using your name.
For a comprehensive understanding of phishing, its various types, and the efforts made by federal law enforcement and authoritative sites to combat phishing scams, we have
compiled a detailed analysis. This includes relevant documents and links that shed light on the intricate landscape of phishing and the measures taken to counteract this
pervasive online threat. Stay informed and vigilant to protect yourself from falling victim to these malicious schemes.
Cautions:
Emails or pop-up messages purporting to be from a business or organization you frequently engage with, such as an Internet service provider (ISP), bank, online payment service,
or government agency, should be approached with caution. These messages often prompt you to "update," "validate," or "confirm" your account information, threatening dire
consequences if you fail to comply. It is a best practice to never respond to emails or pop-ups that request your personal or financial information.
Beware of Emails Claiming:
Exercise caution with emails that request your personal details, such as usernames, passwords, or credit card information. These emails commonly redirect users to enter
information on a fake website designed to closely mimic a legitimate one. Even with server authentication, detecting that the website is fake may require considerable skill.
Interesting facts about Phishing :
- Spam-type emails are one of the most common forms of phishing.
- It is estimated that 59 million phishing emails are sent every day, with 1 in 6 being opened.
- Trusteer's study, "Measuring the Effectiveness of In-the-Wild Phishing Attacks," estimates that just one half of one percent of online banking customers are successfully phished. However, these incidents still cause $2.4M to $9.4M in annual losses per one million clients.
- According to PhishTank, over 60 percent of the 18,000 reported phishes by members in March 2010 were verified in a medium time of 4.5 hours.
- According to McAfee, 95 percent of phishing emails pretend to be from Amazon, eBay, or banks.
- A study by Trusteer estimates that mail-server spam and phishing filters stop 63 percent of phishing emails from reaching inboxes.
- Phishing is often conducted by organized crime.
List of Phishing types :
Clone Phishing :

Clone Phishing is a sophisticated method of executing phishing scams. In this technique, a genuine and previously delivered email, which includes an
attachment or link, is exploited. The content and recipient addresses of the email are extracted and utilized to craft an almost identical or cloned email.
This cloned email is then manipulated by replacing the original content with malicious attachments. Subsequently, it is sent under a spoofed email address,
giving the appearance of authenticity.
Content-Injection Phishing :

Content injection is a form of phishing scam in which the hacker introduces or modifies content, aiming to create links or redirects to another page through a reputable
website. The intention behind this phishing scam is to deceive the target, leading them to a page where they are prompted to enter their personal information, which is
then compromised by the phisher.
Data theft phishing :
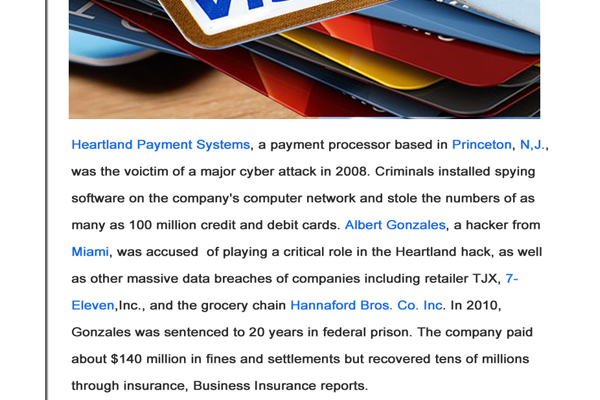
Data theft is a common objective in phishing attacks, focusing on pilfering confidential information from corporations, such as crucial design documents,
confidential memos, and company data. The primary purpose of data theft is often to inflict harm on the target or to sell the stolen information to competitors.
Like other forms of phishing scams, data theft can occur through the deployment of malicious code on any computer, gaining access to activation keys for
expensive software and sensitive information like passwords and account numbers.
Deceptive Phishing :

Deceptive phishing is a scam in which the phisher sends bulk email messages that manipulate users into clicking on specific links provided in the email.
This type of phishing attack is widespread, targeting users to disclose their confidential information. Examples of deceptive phishing include messages
claiming the need to verify account information, notifications of fictitious account charges, alerts about system failures requiring users to re-enter
confidential details, and enticing offers for new services that demand immediate action.
DNS-Based Phishing ("Pharming") :

In DNS-based phishing, phishers manipulate the target's host files and domain name system, causing requests for URLs or name services to return a fake address.
Subsequent communications are then directed to a fraudulent site controlled by hackers. As a result, users are unaware that the website where they are entering
confidential information is controlled by hackers and may not even be in the same country as the legitimate website. The term "pharming" is used to describe domain
name-based phishing.
Email / Spam Phishing :

Email/spam is one of the most common and oldest types of phishing attacks. In this kind of attack, phishers aim to obtain sensitive information such as
usernames, passwords, and credit card numbers from users. Scammers traditionally used email as a means to send messages that convince users to enter their
confidential information. The emails are crafted in a way that forces the user to believe in the deceptive content.
Evil Twins :

"Evil twin" is a term used for a Wi-Fi attack that shares similarities with spoofing or email phishing. This type of phishing scam is best described as wireless
phishing. A phisher deceives the user by connecting to a mobile or laptop and appearing as a legitimate provider. Essentially, this type of phishing attack is
employed to steal passwords by snooping on the communication link.
Hosts File Poisoning :

Host file poisoning is a type of scam where hackers attack the host file and transmit a bogus address, leading the user unwittingly to a fake look-alike
website where their credentials are stolen. Phishers exploit this by taking advantage of the fact that the majority of websites run on the Microsoft Windows
operating system, which first looks up the host name before engaging the DNS (Domain Name Server). The goal of phishers in this type of phishing scam is
to steal the user's information by poisoning the host files.
Instant Messaging :

Instant Messaging is a type of phishing attack similar to email phishing. In this scenario, the user receives a message from the phisher containing
information and a link that redirects the user to a phishing website. The information is crafted in a way to induce the user to click the link. The
subsequent webpage is designed to closely mimic the appearance of the legitimate website. If the user doesn't carefully check the URL, distinguishing
between the original and fake phishing websites can be challenging. The phisher then collects the user's information on the fraudulent phishing webpage.
Key-loggers and Screen-loggers :

Screen Loggers and Key Loggers are specific types of malware that track the keyboard input made by the user and then transmit this information to the
phisher via the internet. These malware entities typically embed themselves into the user's browsers as small utility programs that automatically run
upon the browser's initiation. Referred to as helper objects, these malwares can also infiltrate system files, masquerading as device drivers or screen
monitors. The provided screenshot serves as an illustration of a real-time phishing scam executed through key logging.
Link Manipulation :
Link Manipulation is a technique wherein the phisher sends or includes a link to a well-known and popular website. If the user clicks on the deceptive link,
they are redirected to the phishing page. Phishers also incorporate backlinks to popular pages, redirecting them to their fraudulent pages that mimic
legitimate ones. Identifying these deceptive URLs can be challenging for users, as phishers often redirect the URL after it has been clicked.
Malware Phishing :

Malware phishing is a technique that focuses on executing malware files on the user's computer. These malware files are typically sent as attachments or
downloadable files that activate upon being clicked. Phishers design malware programs capable of causing damage to the user's data and transmitting sensitive
information from the user's computer to the phisher via email.
Malware Based Phishing :
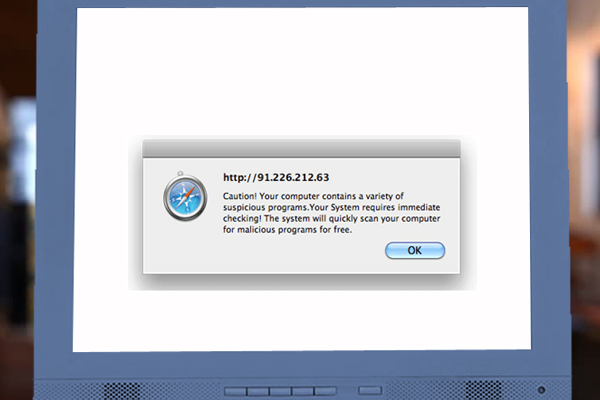
Malware-based phishing is a type of phishing scam wherein the phisher successfully executes malicious software on the user's (target) PC. This malware is
designed to identify confidential information stored on the user's PC or track information entered by the user. These malwares are introduced into the
target system through various means such as email attachments, downloadable files from the web, or by exploiting known security vulnerabilities.
Man-in-the-Middle Phishing :

Man-in-the-middle phishing is a type of phishing that is the most challenging to detect. In this form of phishing scam, the phisher positions themselves between the user
and the original website or system. They record the information entered by the user and seamlessly pass the user through regular transactions to avoid suspicion. Once
the process is complete, the phisher then utilizes or sells the recorded information.
Mass Phishing :
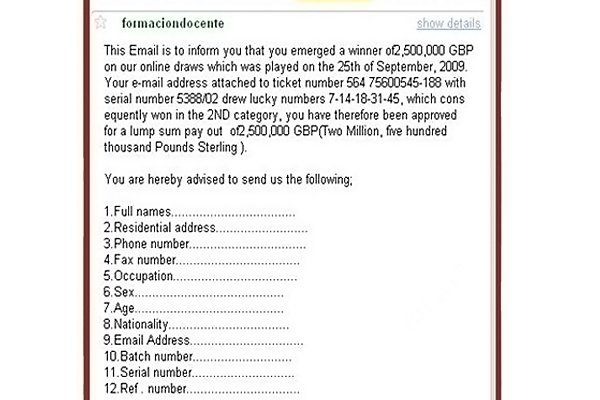
A mass phishing attack is aimed at a broad target audience, whether or not they are related to the service mail that is sent. The intention of the phisher
is to attack as many users as possible. The scammer does not bother about who opens the mail and who does not. This kind of phishing attack is executed to
cover a vast amount of audience, and the probability of success is determined later. Mass phishing is analogous to throwing a fishing net with the intention
of catching as many target fishes as possible.
Phone Phishing :
Phone phishing is another type of phishing scam where the phisher makes phone calls to users and prompts them to dial numbers that request verification of
user information. When the user dials or presses for account or credit card information verification, the phisher seizes the required information to
conduct fraudulent transactions. This form of phishing is typically carried out using fake caller IDs. However, phone phishing is less popular these days
due to tightened security systems.
Search Engine Phishing :
Search engine phishing is a type of phishing scam where phishers create enticing websites to lure customers into entering their personal information. These
websites are designed to be legitimately indexed by search engines, leading users to encounter them during their normal search activities. An example of
search engine phishing could be a website posing as a banking site offering additional benefits beyond what a typical bank provides. Customers are enticed
to enter their data, only to end up deceived.
Session Hijacking :

With the surge in the popularity of e-commerce websites and online banking transactions, a type of phishing scam known as "Session Hijacking" has emerged.
In this scam, the activities of users are monitored until they log into a vulnerable area, such as the checkout process on shopping websites or a banking
site, where the user enters their credentials. At these moments, malicious software takes control and executes unauthorized actions, such as transferring
funds or hacking credit card details, without the user's knowledge.
Spear Phishing :
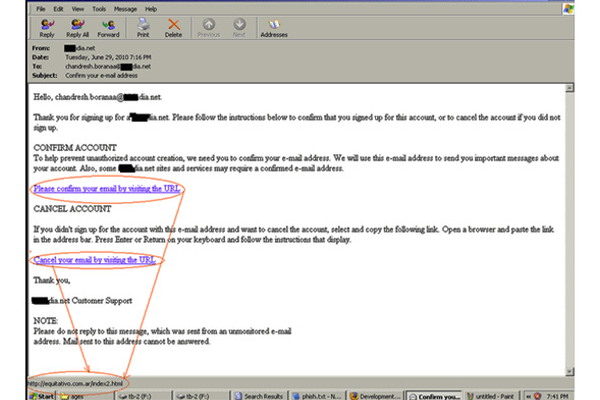
Spear Phishing is currently the most successful type of phishing scam on the internet. In this phishing attack, phishers gather all the necessary information
about the target. It is typically directed towards specific individuals or companies. A spear phisher collects detailed information about the target to
enhance the probability of the attack's success. Spear phishing attacks are not initiated by "random hackers" but are more likely to be perpetrated by
individuals with specific goals.
Spy phishing :
Spy phishing is one of the latest phishing scams that combines techniques from phishing and spyware. Coined by Jeffery abound in 2006, the term "spy phishing"
involves using spyware to steal user information through prolonged phishing attacks. In these attacks, the spyware remains dormant until the user enters
vulnerable areas, at which point it initiates the attack on the user's system.
System Reconfiguration Phishing :
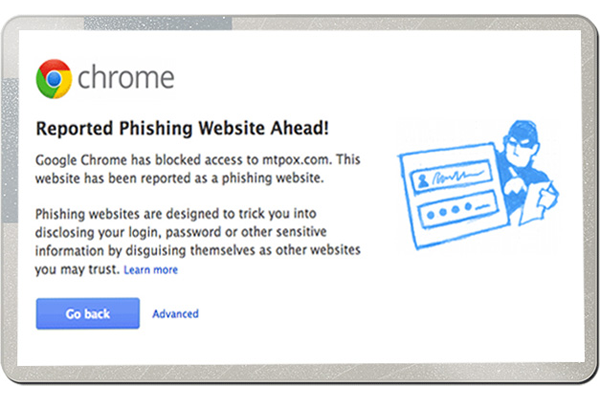
System Reconfiguration, as the name suggests, is a type of phishing attack where the system settings of the target's PC are modified for malicious purposes.
A common example of a system reconfiguration attack involves altering URLs and directing them towards similar-looking or sounding URLs with the intention of
tricking the user into a phishing attack. For instance, the URL of the user's bank, which is frequently used, may be stored in the "favorites" section or
may be changed to a similar-looking URL that the user might not pay much attention to.
Tabnabbing :

Tabnabbing is one of the recent phishing scams discovered in the early 2010 by Aza Raskin. Unlike other phishing scams, Tabnabbing works in reverse order.
Instead of influencing the user to click on a link to obtain their credentials, the phisher loads a fake page in one of the open tabs in the user's browser,
hence the name "Tabnabbing."
Web based delivery :

Web-based delivering phishing is one of the most sophisticated phishing techniques ever known. It is very similar to the "man in the middle" phishing technique,
where the phisher is located between the original website and the targeted user. In this type of phishing scam, the usual process of the user is not
interrupted, making the user believe that nothing is going wrong. As the user continues to enter sensitive information, the phisher in the middle collects
all the necessary information, thus making the phishing attack successful without the knowledge of the user.
Whaling :

Whaling is a term given to a phishing attack where senior executives and other high-profile individuals are targeted. In recent times, it has been observed
that most phishing attacks are directed at senior high-profile people in the business industry. The content of a whaling attack email typically includes
legal documents and executive-related issues. Whaling phishers often forge official-looking emails and documents, urging the user to click on an intended
link to spread malware. In the screenshot below, the user is directed to click the link, leading to the download of masquerading software that accesses
the user's private information.
Web Trojans

Web Trojans are a type of phishing scam where the phishing process is designed in the form of pop-ups that appear invisibly when users attempt to log into
any vulnerable area. These pop-ups collect the information entered by the user and transmit it to the phisher via the internet. Web Trojans are basically
designed to collect user credentials through a local machine. The screenshot below serves as an example of a Web Trojan pop-up, where the fields highlighted
in red are additional fields injected to acquire the user's personal information. Once this data is entered by the target, it is transferred to the command
and control host.






















