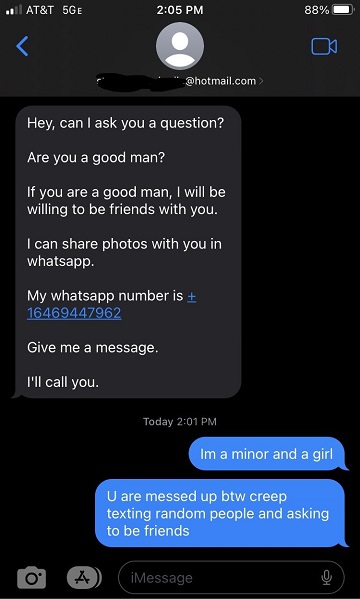
Sextorian Scams
Sextortion scams are a type of cybercrime where the scammers threaten to distribute explicit images or videos of the victim unless they agree to their demands, which might include monetary payments or additional explicit content. Often, these scams begin with the perpetrator gaining trust and then exploiting it to acquire compromising material.
Sextortion Scams: Understanding a Cyber Threat
Sextortion scams represent a form of cybercrime in which perpetrators leverage explicit images or videos of the victim to coerce compliance with their demands. These demands typically involve monetary payments or the submission of additional compromising content. The modus operandi of such scams often entails the initial establishment of trust by the perpetrator, followed by its exploitation to obtain compromising material.
This insidious form of online extortion underscores the importance of heightened cybersecurity awareness and vigilance in safeguarding personal information and privacy. It is crucial for individuals to remain informed about potential threats and adopt proactive measures to mitigate the risks associated with such malicious activities.
Operational Mechanics of Sextortion Scams
Step 1: Target Selection
Scammers meticulously identify their targets, often focusing on individuals who exhibit signs of vulnerability, loneliness, or limited experience in online interactions.
Step 2: Establishing Trust
1. Initiating Contact:
Scammers initiate contact through various channels such as social media platforms, dating apps, or email, assuming roles as interested partners or friends.
2. Cultivating Relationships:
The scammer invests time in cultivating what appears to be an authentic relationship, engaging in regular conversations, and expressing a genuine interest in the victim's life.
Step 3: Manipulation and Coercion
1. Escalating Conversations:
Once trust is established, conversations progress to more personal and often sexual subjects. The scammer may share explicit content of themselves to encourage reciprocal actions from the victim.
2. Soliciting Explicit Content:
The scammer requests explicit photos or videos from the victim, employing manipulative language or coercive tactics.
Step 4: The Threat Phase
1. Threat of Exposure:
After obtaining explicit content, the scammer unveils their true intentions, threatening to disseminate the material to the victim's family, friends, or workplace unless specific demands are met.
2. Demands:
These demands typically involve monetary requests, often requiring substantial sums to be transferred through untraceable methods such as cryptocurrency. Alternatively, they might insist on additional explicit content.
Step 5: Continued Exploitation
Scammers may persist in exploiting the victim, utilizing the acquired material to exert control and extract further resources.
Step 6: Potential Outcomes
1. Vanishing Act:
Upon receiving payment or content, the scammer may disappear, redirecting their efforts to target another individual.
2. Sustained Manipulation:
In other instances, the scammer may sustain contact, leveraging the acquired material to perpetuate the exploitation of the victim.
Identification of Early Indicators: Safeguarding Against Sextortion Scams
Preserving your security necessitates a keen awareness of the preliminary signs indicative of a sextortion scam. These may encompass:
- Unexpected Attachments or Links: Exercise caution when encountering unsolicited messages containing attachments or links.
- Rapid Relationship Progression: Scammers often employ expedited relationship development to swiftly cultivate trust.
- Solicitation of Explicit Content: Exercise caution when faced with individuals pressuring you for explicit material.
- Threats and Blackmail: Stay vigilant against scammers resorting to threats and blackmail, exploiting acquired material for coercive purposes.
Adopt the following measures to fortify yourself against the threat of falling victim to sextortion scams:
- Safeguard Your Personal Information: Exercise caution when divulging personal information to individuals encountered online.
- Refrain from Sharing Explicit Content: Abstain from sharing explicit images or videos with anyone, even in cases where trust may be presumed.
- Enhance Device Security: Ensure the robust security of your devices by employing strong, unique passwords.
- Prompt Reporting to Authorities: If you harbor suspicions of being targeted, promptly report the situation to the relevant authorities.
Additionally, consider the following supplementary precautions:
- Employ Two-Factor Authentication: Bolster your account security by implementing two-factor authentication where feasible.
- Regularly Update Security Software: Keep your antivirus and anti-malware programs up to date to fortify your defense against potential cyber threats.
- Exercise Caution with Online Connections: Scrutinize and validate the legitimacy of individuals you connect with online, particularly on platforms that facilitate interpersonal interactions.
- Educate Yourself: Stay informed about evolving online threats and scams, empowering yourself with the knowledge needed to identify and thwart potential risks.
Guidelines for Responding If You Become a Target
In the unfortunate event that you become the target of a sextortion scam, adhere to the following course of action:
- Refrain from Engagement: Exercise restraint by avoiding negotiations or any form of communication with the perpetrator.
- Document Incidents: Methodically preserve evidence by maintaining a record of messages and any other relevant proof of the scam.
- Report the Incident: Swiftly report the incident to both local law enforcement and the respective online platforms involved.
- Seek Emotional Support: Reach out to support groups or counseling services to navigate the emotional challenges stemming from the situation.
Remember, taking decisive and prompt action can be pivotal in mitigating the impact of a sextortion attempt and safeguarding your well-being.
Prevent Against Sextortion Scams
Sextortion scams represent a reprehensible exploitation, capitalizing on fear and vulnerability. By attuning yourself to the warning signs and implementing proactive measures, you can fortify your defenses against falling prey to these malicious schemes. Always prioritize online safety, navigating the digital realm with prudence and vigilance.
Remain vigilant, stay secure, and actively contribute to fostering a culture of awareness and protection against online exploitation. Your commitment to these principles contributes to creating a safer digital environment for everyone.
Guidelines on Reporting a Sextortion Scam
How to Report a Sextortion Scam
Step 1: Maintain Composure
It is crucial to remain calm. Scammers often exploit panic to coerce victims into impulsive actions.
Step 2: Preserve Critical Evidence
Prioritize the collection of evidence by taking screenshots of all messages, emails, or any other form of communication. Save pertinent files or links, as this evidence serves as a vital component for reporting the scam.
Step 3: Avoid Further Engagement
It is advisable to cease communication with the scammer. Refrain from making payments or engaging in negotiations, as these actions rarely guarantee your safety and may render you susceptible to future scams.
Step 4: Report to Local Authorities
Initiate the reporting process by visiting your local police station or cybercrime unit. Provide them with all the gathered evidence for a comprehensive investigation.
Step 5: Report to Online Platforms
If the scam occurred on a specific platform, such as Facebook, Twitter, or an email service, use the reporting tools provided by the platform to report the user and the incident. Refer to links like StopNCII for platform-specific reporting, especially if the incident involves Meta.
Step 6: Seek Support from a Support Group
Recognize the emotional toll of sextortion and consider reaching out to local or online support groups that offer counseling or assistance.
Step 7: Educate and Inform
After taking necessary precautions, share your experience with trusted friends and family. Educating those around you can contribute to preventing them from falling victim to similar scams.
Remember: Prioritize your safety and well-being. Throughout this process, emphasize the importance of maintaining your mental and emotional health.