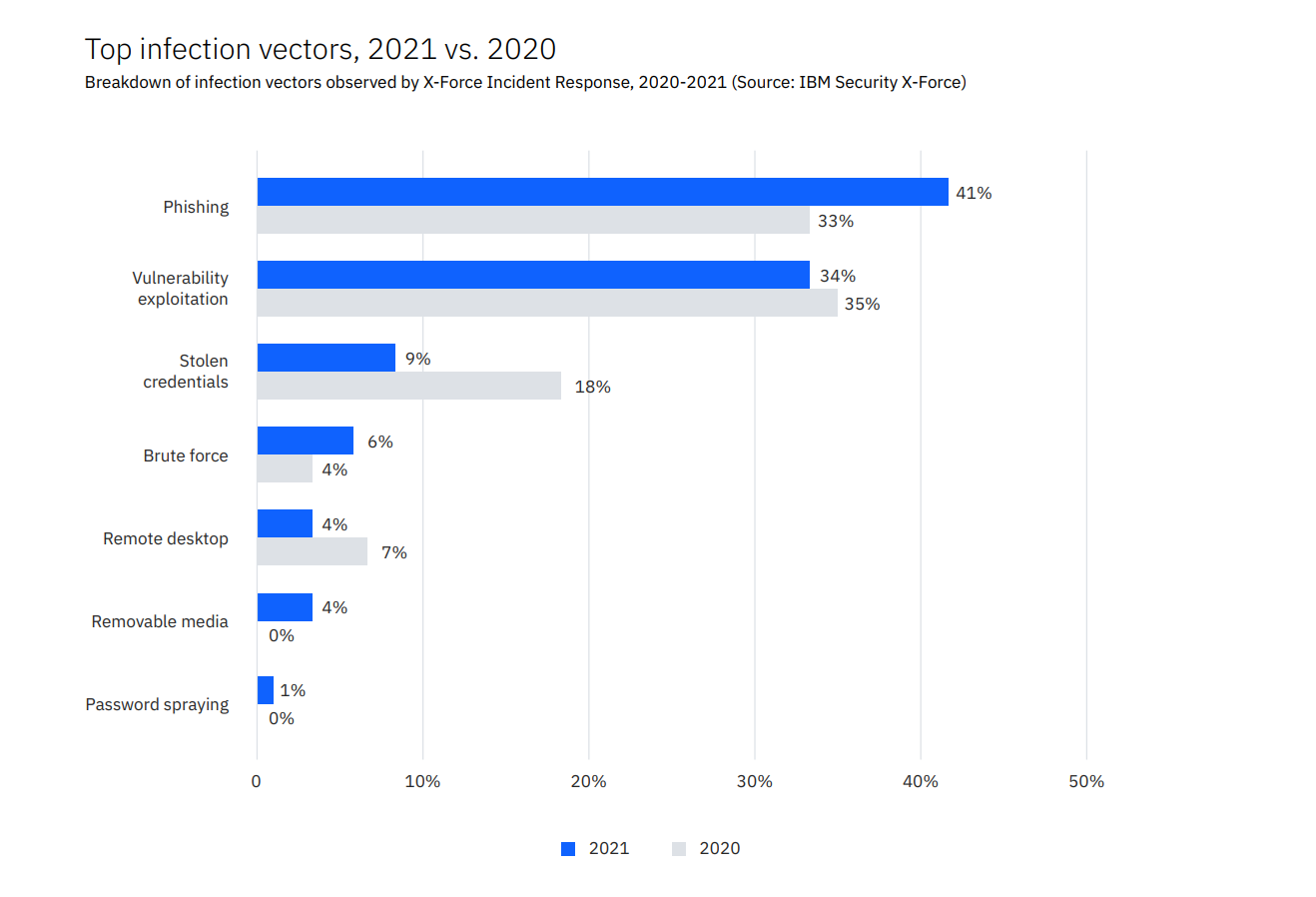
Vishing Scam
Vishing is a type of scam in which criminals use social engineering techniques to try to gain access to private and sensitive information, such as credit card numbers, bank account details and passwords, by pretending to be a legitimate company or organization. They often use automated telephone calls (often referred to as "robocalls") to trick people into giving up information. They may also use text messages or emails to lure their victims into clicking on malicious links or attachments.
How can vishing be prevented?
Be suspicious of any unsolicited calls, emails, or text messages asking for personal or financial information.
Do not respond to requests for personal information, no matter how urgent they may seem.
Do not trust caller ID. Fraudsters can spoof numbers to make them appear to be from a trusted source.
Use strong passwords and change them frequently.
Use two-factor authentication whenever possible.
Do not click on links or download attachments in unsolicited emails or text messages.
Make sure anti-virus software and other security measures are up to date.
Use only secure websites when entering personal or financial information online. Look for "https" in the URL.
Educate yourself and your employees about common phishing and vishing tactics.
Report any suspicious calls or messages to your financial institution.
Vishing is a type of scam that involves criminals using telephone calls, emails, text messages or other forms of communication to try and get victims to reveal sensitive information such as passwords, credit card numbers, account numbers or other confidential information. Vishing scams typically involve fraudsters posing as representatives from legitimate companies or organizations in order to gain access to victims' personal information. Victims are often tricked into providing the requested information through various methods, such as phishing emails, automated phone calls, or messages sent through social media.
What are the risks in vishing ?
Identity Theft: Vishing scams often involve collecting sensitive personal information such as Social Security numbers, credit card numbers, and bank account numbers. This can be used to commit identity theft, which can result in significant financial losses.
Phishing: Vishing scams are often used as a form of phishing, which is a type of attack that attempts to trick users into revealing personal information by impersonating a trusted entity.
Malware: Vishing scams can be used to install malware on a victim's computer. Malware can be used to steal data or to launch attacks against other systems.
Loss of Money: Vishing scams can be used to gain access to bank accounts or other financial information, which can result in the loss of money.
Social Engineering: Vishing scams can be used to manipulate individuals into revealing sensitive information or taking certain actions. This can be used to gain access to accounts or to commit other types of fraud.
What are some common methods used in vishing attacks?
Spoofing caller ID: Attackers can spoof their caller ID to appear as though they are calling from a legitimate source, such as a bank or government agency.
Social engineering: Attackers use social engineering to build trust and persuade victims to provide sensitive information.
Phishing: Attackers send out emails or text messages that appear to come from a legitimate source, such as a bank or government agency, and contain malicious links or attachments.
Voicemail phishing: Attackers leave pre-recorded messages on victims' voicemail boxes, inviting them to call a certain phone number and provide sensitive information.
Caller ID spoofing: Attackers use caller ID spoofing technology to disguise their phone numbers and make it appear as though it is coming from a legitimate source.

Vishing typically happens when an attacker sends an email or text message to a victim that appears to be from a legitimate source. The message may contain a link or attachment that, when clicked on, directs the victim to a malicious website or downloads malicious software onto their device. The malicious website or software then allows the attacker to gain access to the victim's personal information, such as bank account numbers, passwords, or credit card numbers.
Types of Vishing?
Voicemail Vishing: A scammer leaves a voicemail message asking the recipient to call a certain number to verify sensitive information.
Email Vishing: A scammer sends an email with a link to a website that appears to be legitimate, but is actually a malicious site designed to steal personal information.
SMS Vishing: A scammer sends a text message asking the recipient to call a certain number to verify sensitive information.
Social Media Vishing: A scammer contacts the target through social media and asks them to provide sensitive information or to click on a malicious link.
Telephone Vishing: A scammer calls the target and attempts to obtain personal information or convince the target to transfer money.
Vishing is a type of social engineering attack in which attackers use telephone calls or voice messages to try to deceive targets into providing confidential information or making payments. Vishing scams can involve using automated calls or spoofed caller IDs to try to appear legitimate.
In a typical vishing attack, the attacker will use a pre-recorded message to try to convince the target to provide sensitive information, such as bank account numbers, credit card information, or passwords. The attacker may also try to get the target to make a payment or transfer money.
Common vishing tactics to listen for :
Threats and urgency – scammers might try to create a sense of urgency or threaten victims with legal repercussions or account deactivation if they don't provide personal or financial information.
Impersonation – scammers might try to convince victims they are speaking with a legitimate representative from a bank, government agency, or other organization.
Offering rewards – scammers might try to entice victims by offering rewards or free gifts in exchange for personal or financial information.

False authority – scammers might try to use language or titles to appear more legitimate or authoritative.
Too good to be true – scammers might offer deals that sound too good to be true, such as a free service or a large sum of money for nothing.
Unsolicited contact – scammers might contact victims without any prior interaction.
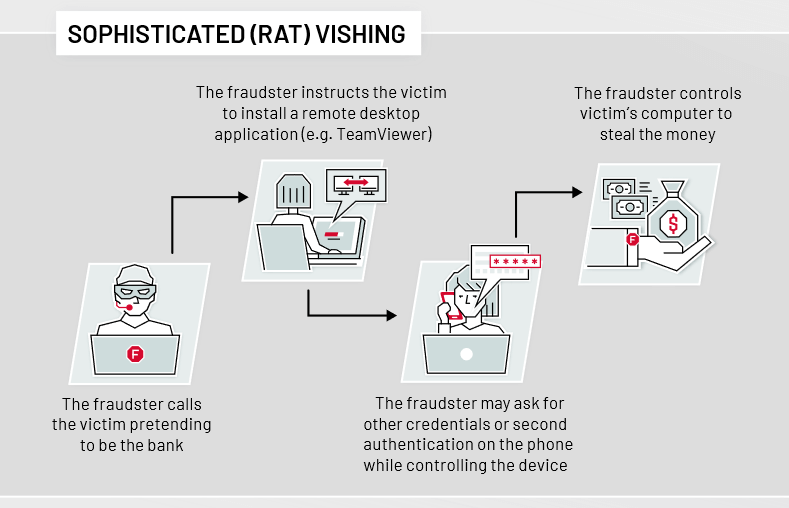
How to Spot a Vishing Scam :
Be suspicious of unexpected calls or emails asking for sensitive information. Legitimate organizations will never ask for financial information, passwords, or other personal details over the phone or via email.
Be suspicious of callers who claim to represent a company but don't provide an employee ID number.
Be wary of callers who claim to be from government organizations asking for financial information. Government organizations will never ask for personal or financial information over the phone.
Be suspicious of callers who are overly pushy or demanding. Legitimate organizations will not pressure you into providing information or making a decision quickly.
If you get an unexpected call or email asking for sensitive information, hang up the phone or delete the email and contact the organization directly to verify the request.
If you get a call from someone claiming to be from a company you do business with, hang up and call that company directly using the number found on their website or in an official document.